CCNP300-410学习笔记(51-100)
51、Refer to the exhibit. Network operations cannot read or write any configuration on the device with this configuration from the operations subnet. Which two configurations fix the issue? (Choose two.)
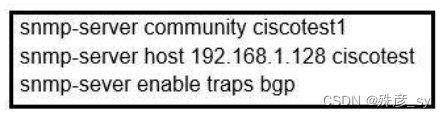
A. Configure SNMP rw permission in addition to community ciscotest.
B. Modify access list 1 and allow operations subnet in the access list.
C. Modify access list 1 and allow SNMP in the access list.
D. Configure SNMP rw permission in addition to version 1.
E. Configure SNMP rw permission in addition to community ciscotest 1
52、Refer to the exhibit. Why is the remote NetFlow server failing to receive the NetFlow data?
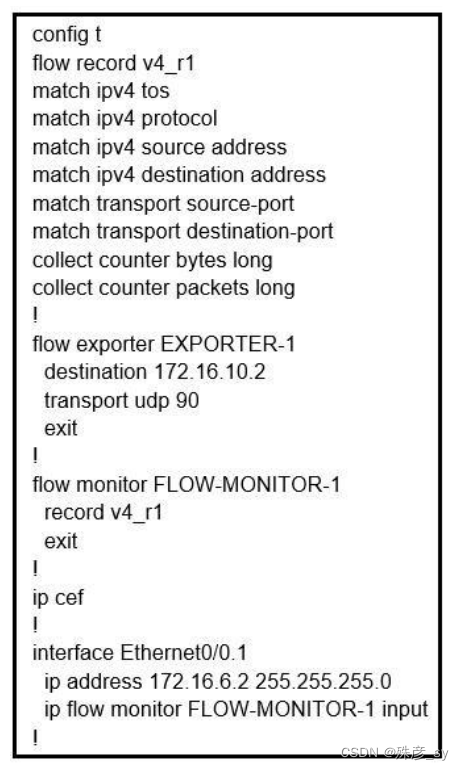
A. The flow exporter is configured but is not used.
B. The flow monitor is applied in the wrong direction.
C. The flow monitor is applied to the wrong interface.
D. The destination of the flow exporter is not reachable.
53、Drag and drop the MPLS VPN concepts from the left onto the correct descriptions on the right
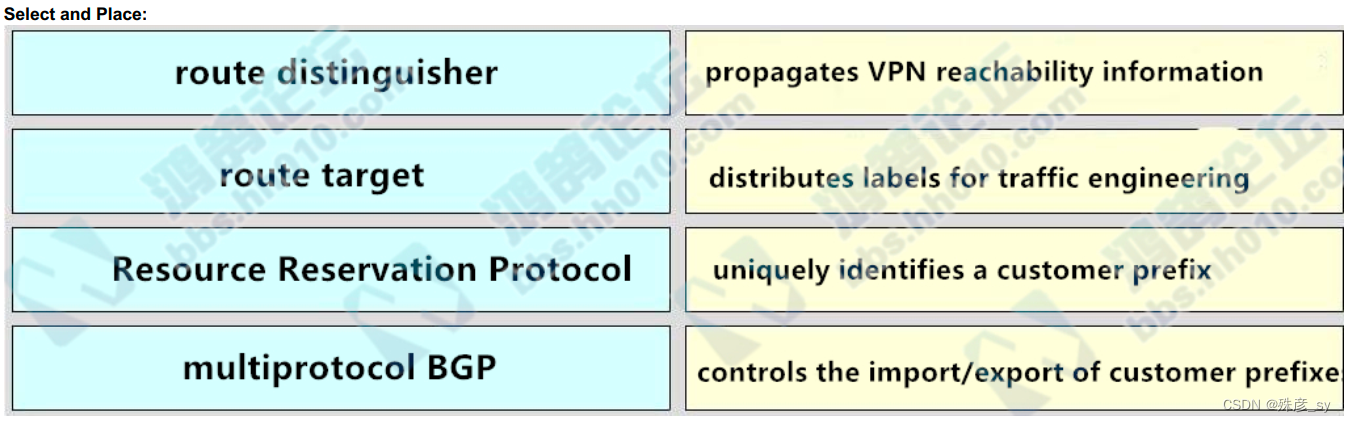
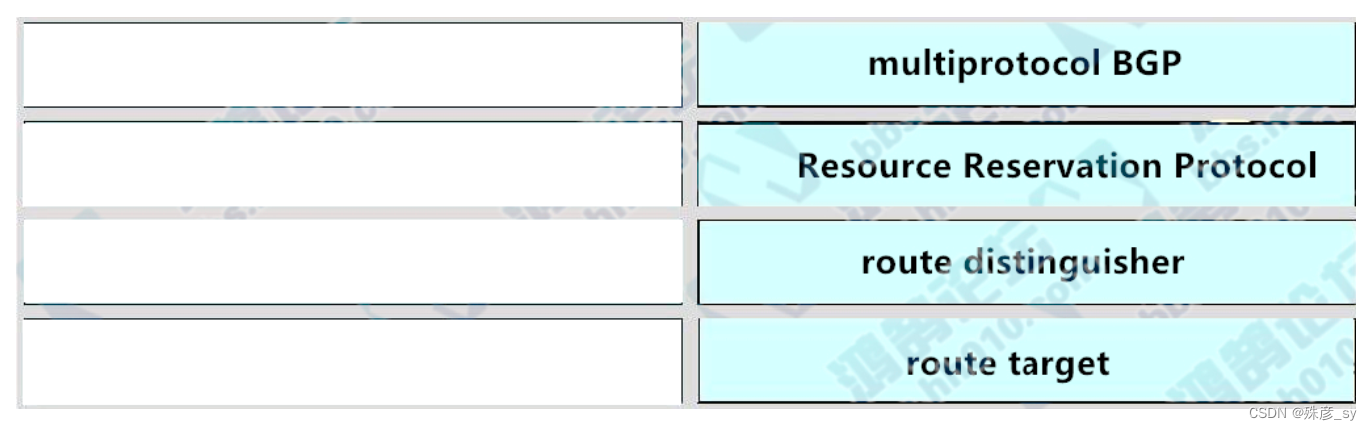
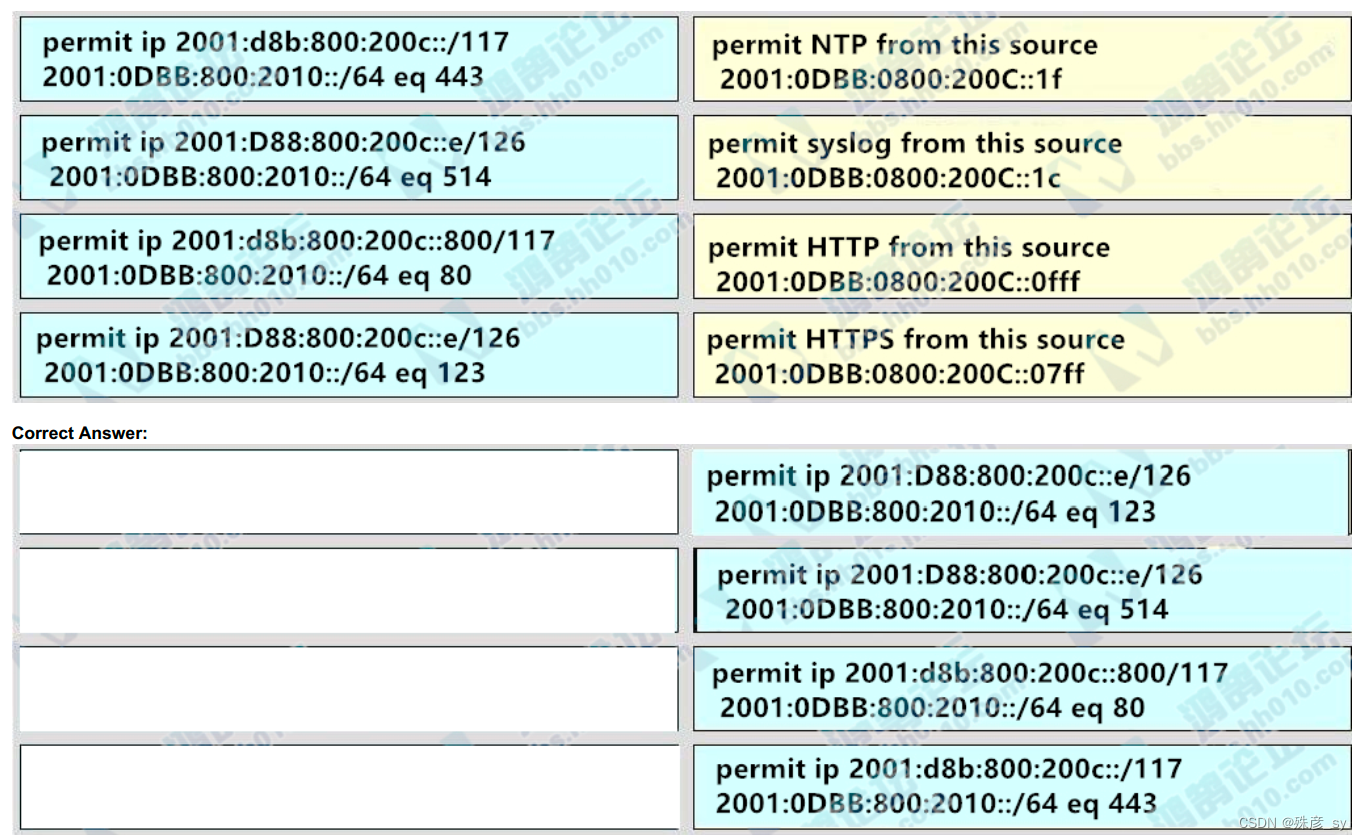
54、Drag and drop the addresses from the left onto the correct IPv6 filter purposes on the right.
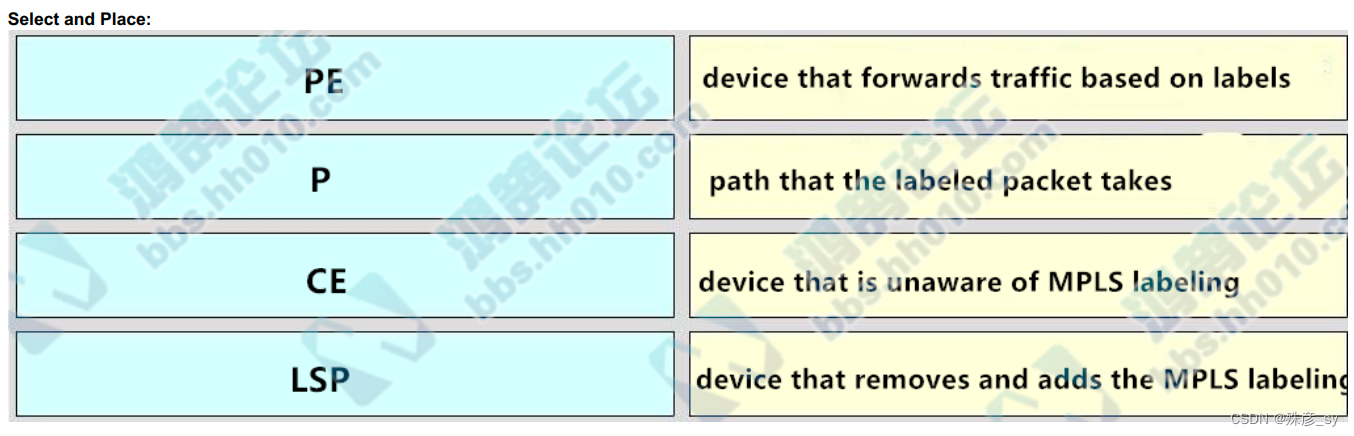
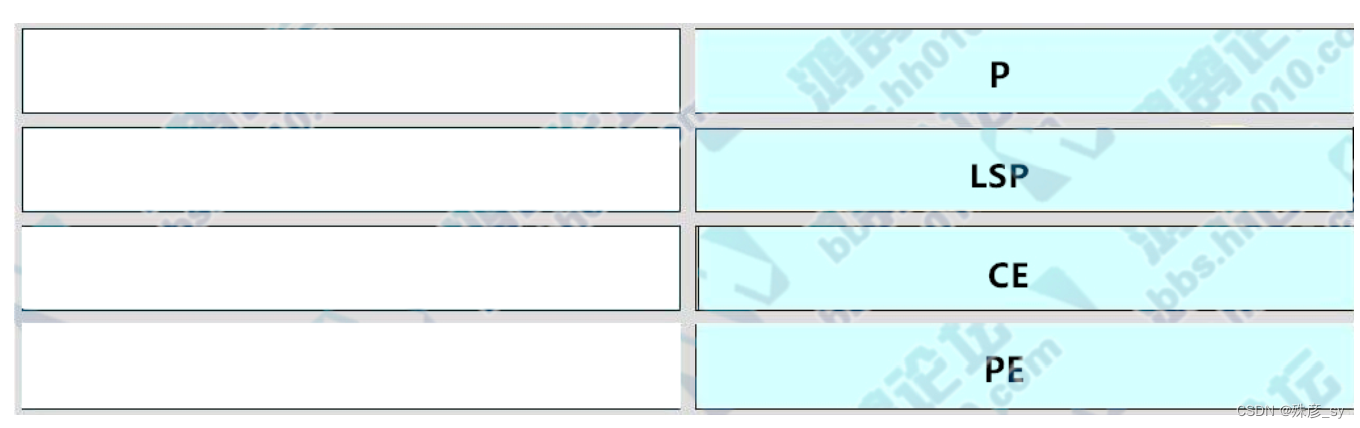
55、Drag and drop the MPLS terms from the left onto the correct definitions on the right.
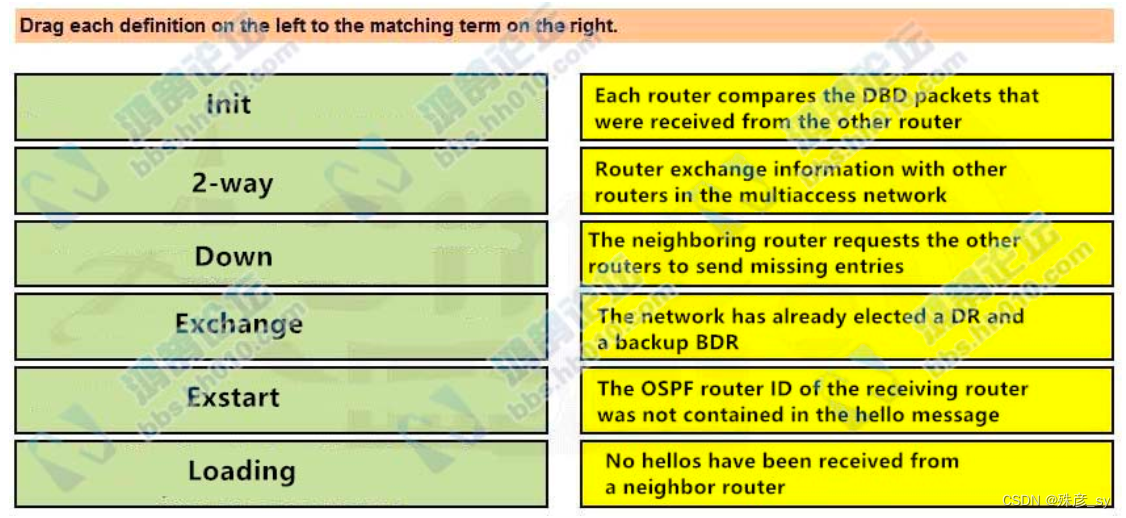
56、Drag and drop the OSPF adjacency states from the left onto the correct descriptions on the right.
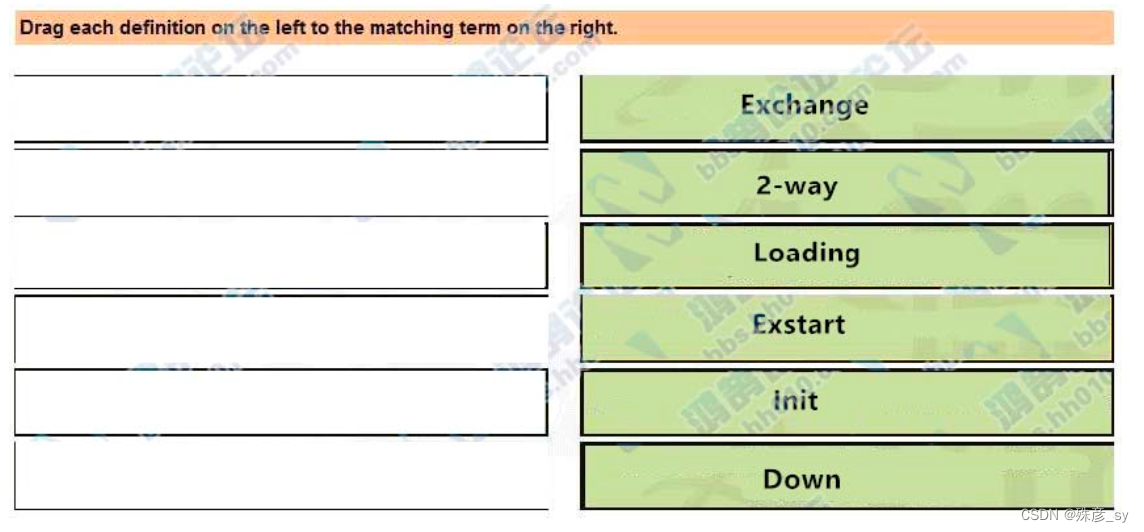
57、Drag and drop the DHCP messages from the left onto the correct uses on the right
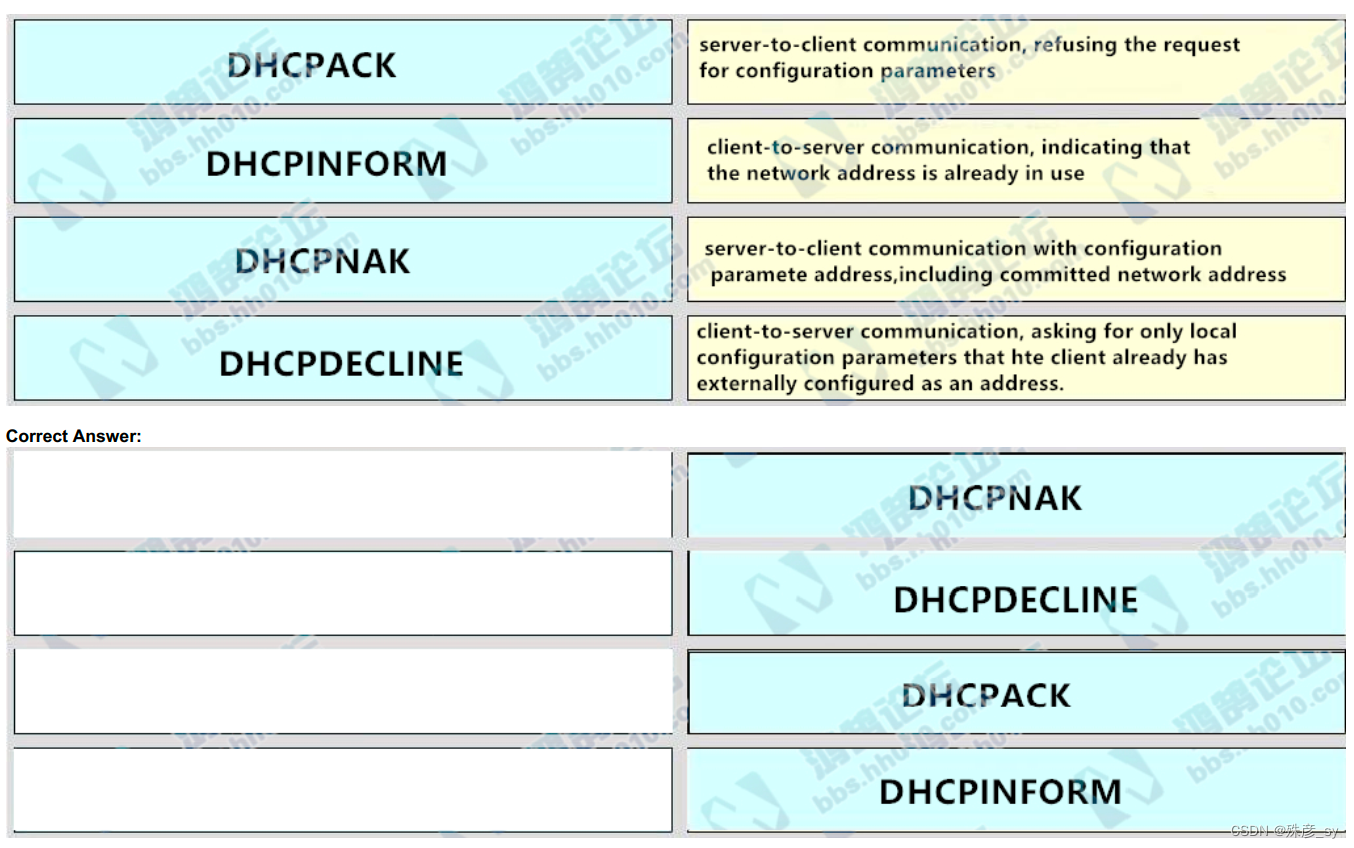
58、Drag and drop the packet types from the left onto the correct descriptions on the right.
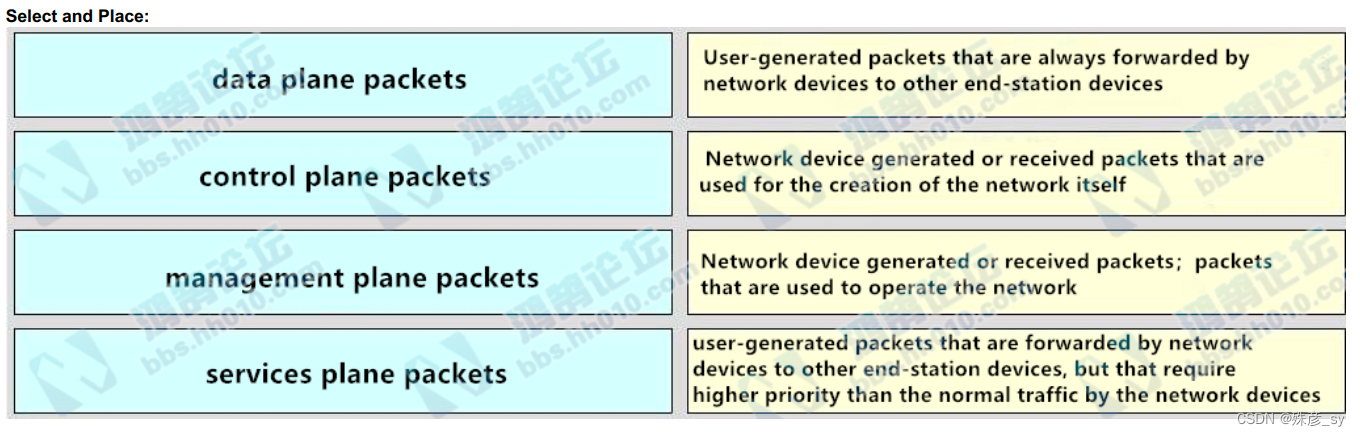
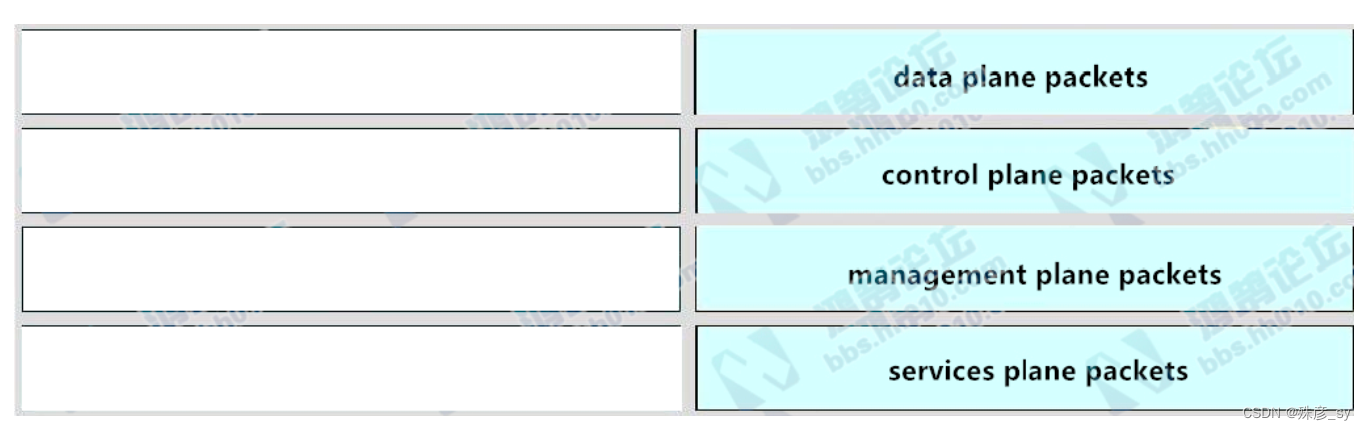
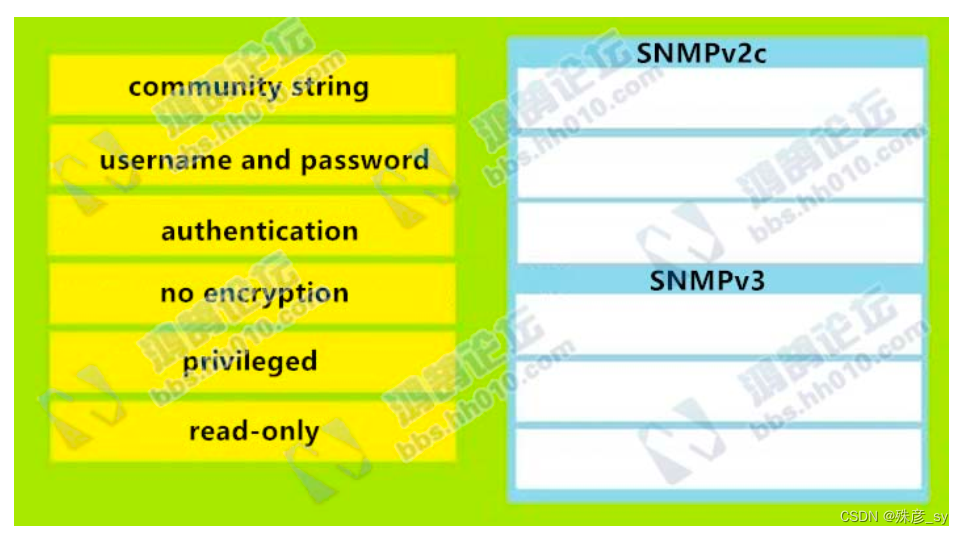
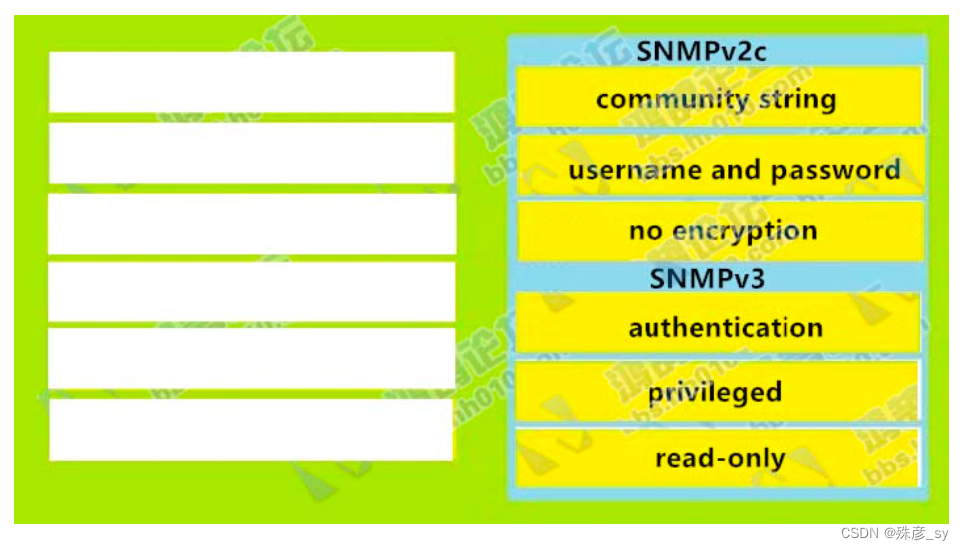
59、Drag and drop the SNMP attributes in Cisco IOS devices from the left onto the correct SNMPv2c or SNMPV3 categories on the right.
60、Refer to the exhibit.
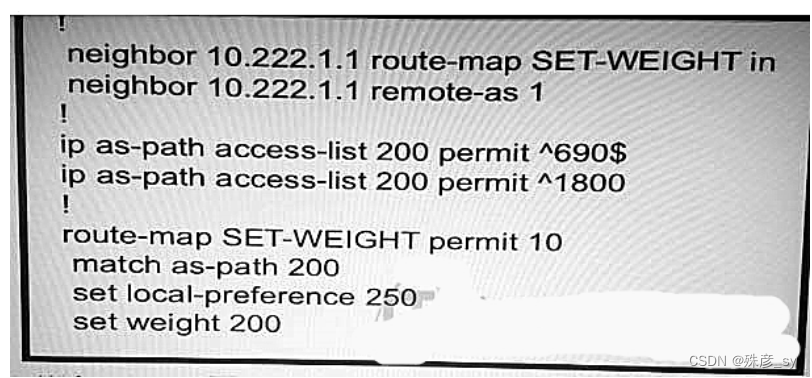
A router receiving BGP routing updates from multiple neighbors for routers in AS 690. What is the reason that the router still sends traffic that isdestined to AS 690
to a neighbor other than10.222.10.1?
A. The local preference value in another neighbor statement is higher than 250.
B. The local preference value should be set to the same value as the weight in the route map.
C. The route map is applied in the wrong direction.
D. The weight value in another statement is higher than 200.
61、 Which security feature can protect DMVPN tunnels?
A. IPsec
B. TACACS+
C. RTBH
D. RADIUS
62、Which two methods use IPsec to provide secure connectivity from the branch office to the headquarters office? (Choose two.)
A. DMVPN
B. MPLS VPN
C. Virtual Tunnel Interface (VTI)
D. SSL VPN
E. PPPoE
63、Which protocol is used in a DMVPN network to map physical IP addresses to logical IP addresses?
A. BGP
B. LLDP
C. EIGRP
D. NHRP
64、Which Cisco VPN technology can use multipoint tunnel, resulting in a single GRE tunnel interface on the hub, to support multiple connections from multiple spoke devices?
A. DMVPN
B. GETVPN
C. Cisco Easy VPN
D. FlexVPN
65、Which option is the best for protecting CPU utilization on a device?
A. fragmentation
B. COPP
C. ICMP redirects
D. ICMP unreachable messages
66、Which SNMP verification command shows the encryption and authentication protocols that are used in SNMPV3?
A. show snmp group
B. show snmp user
C. show snmp
D. show snmp view
67、What is the role of a route distinguisher via a VRF-Lite setup implementation?
A. It extends the IP address to identify which VFP instance it belongs to.
B. It manages the import and export of routes berween two or more VRF instances
C. It enables multicast distribution for VRF-Lite setups to enhance EGP routing protocol capabilities
D. It enables multicast distribution for VRF-Lite setups to enhance IGP routing protocol capabilities
68、Refer to the following output:
Router#show ip nhrp detail
1.1.2/8 via 10.2.1.2, Tunnel1 created 00:00:12, expire 01:59:47 TypE. dynamic, Flags: authoritative unique nat registered used NBMA address:
10.12.1.2
What does the authoritative flag mean in regards to the NHRP information?
A. It was obtained directly from the next-hop server.
B. Data packets are process switches for this mapping entry.
C. NHRP mapping is for networks that are local to this router.
D. The mapping entry was created in response to an NHRP registration request.
E. The NHRP mapping entry cannot be overwritten
69、Which two protocols can cause TCP starvation? (Choose two)
A. TFTP
B. SNMP
C. SMTP
D. HTTPS
E. FTP
70、Which two statements about VRF-Lite configurations are true? (Choose two.)
A. They support the exchange of MPLS labels
B. Different customers can have overlapping IP addresses on different VPNs
C. They support a maximum of 512.000 routes
D. Each customer has its own dedicated TCAM resources
E. Each customer has its own private routing table.
F. They support IS-IS
71、A network engineer needs to verify IP SLA operations on an interface that shows on indication of excessive traffic. Which command should the engineer use to
complete this action?
A. show frequency
B. show track
C. show reachability
D. show threshold
72、Which protocol does VRF-Lite support?
A. S-IS
B. ODR
C. EIGRP
D. IGRP
73、
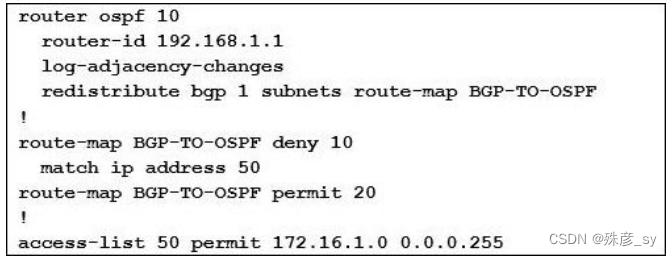
Refer to Exhibit.Which statement about redistribution from BGP into OSPF process 10 is true?
A. Network 172.16.1.0/24 is not redistributed into OSPF.
B. Network 10.10 10.0/24 is not redistributed into OSPF
C. Network 172.16.1.0/24 is redistributed with administrative distance of 1.
D. Network 10.10.10.0/24 is redistributed with administrative distance of 20.
74、Which two statements about redistributing EIGRP into OSPF are true? (Choose two)
A. The redistributed EIGRP routes appear as type 3 LSAs in the OSPF database
B. The redistributed EIGRP routes appear as type 5 LSAs in the OSPF database
C. The administrative distance of the redistributed routes is 170
D. The redistributed EIGRP routes appear as OSPF external type 1
E. The redistributed EIGRP routes as placed into an OSPF area whose area ID matches the EIGRP autonomous system number
F. The redistributed EIGRP routes appear as OSPF external type 2 routes in the routing table
75、

Refer to the exhibit.Which routes from OSPF process 5 are redistributed into EIGRP?
A. E1 and E2 subnets matching access list TO-OSPF
B. E1 and E2 subnets matching prefix list TO-OSPF
C. only E2 subnets matching access list TO-OSPF
D. only E1 subnets matching prefix listTO-OS1
76、 Users were moved from the local DHCP server to the remote corporate DHCP server. After the move, none of the users were able to use the network.Which two
issues will prevent this setup from working properly? (Choose two)
A. Auto-QoS is blocking DHCP traffic.
B. The DHCP server IP address configuration is missing locally
C. 802.1X is blocking DHCP traffic
D. The broadcast domain is too large for proper DHCP propagation
E. The route to the new DHCP server is missing
77、What is the output of the following command: show ip vrf
A. Show's default RD values
B. Displays IP routing table information associated with a VRF
C. Show's routing protocol information associated with a VRF.
D. Displays the ARP table (static and dynamic entries) in the specified VRF
78、Which command is used to check IP SLA when an interface is suspected to receive lots of traffic with options?
A. show track
B. show threshold
C. show timer
D. show delay
79、Refer to the exhibit. AAA server 10.1.1.1 is configured with the default authentication and accounting settings, but the switch cannot communicate with the server.
Which action resolves this issue?
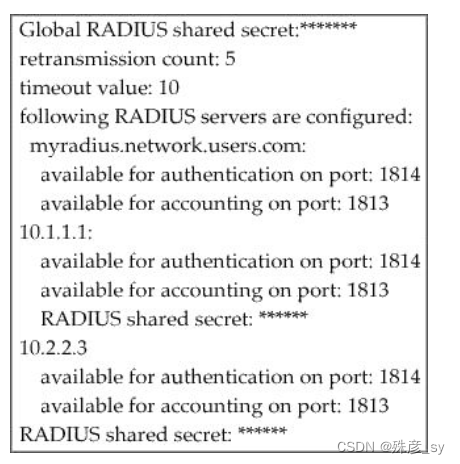
A. Correct the timeout value
B. Match the authentication port
C. Correct the shared secret
D. Match the accounting port
80、 Refer to the exhibit. A company is evaluating multiple network management system tools. Trending graphs generated by SNMP data are returned by the NMS and appear to have multiple gaps. While troubleshooting the issue, an engineer noticed the relevant output. What solves the gaps in the graphs?
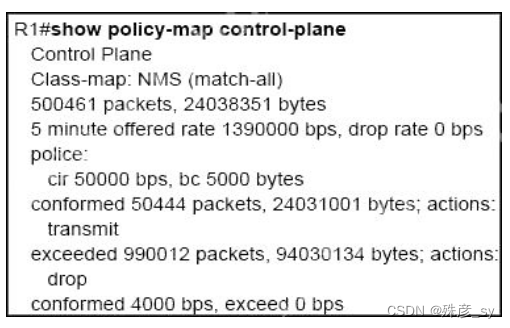
A. Remove the class map NMS from being part of control plane policing
B. Remove the exceed-rate command in the class map
C. Configure the CIR rate to a lower value that accommodates all the NMS tools
D. Separate the NMS class map in multiple class maps based on the specific protocols with appropriate CoPP actions
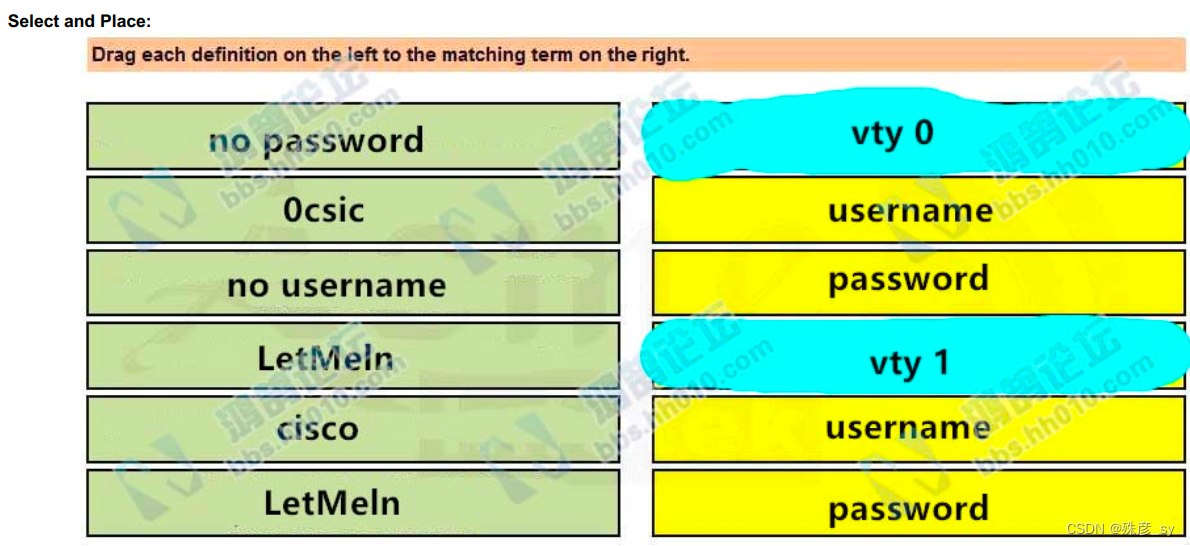
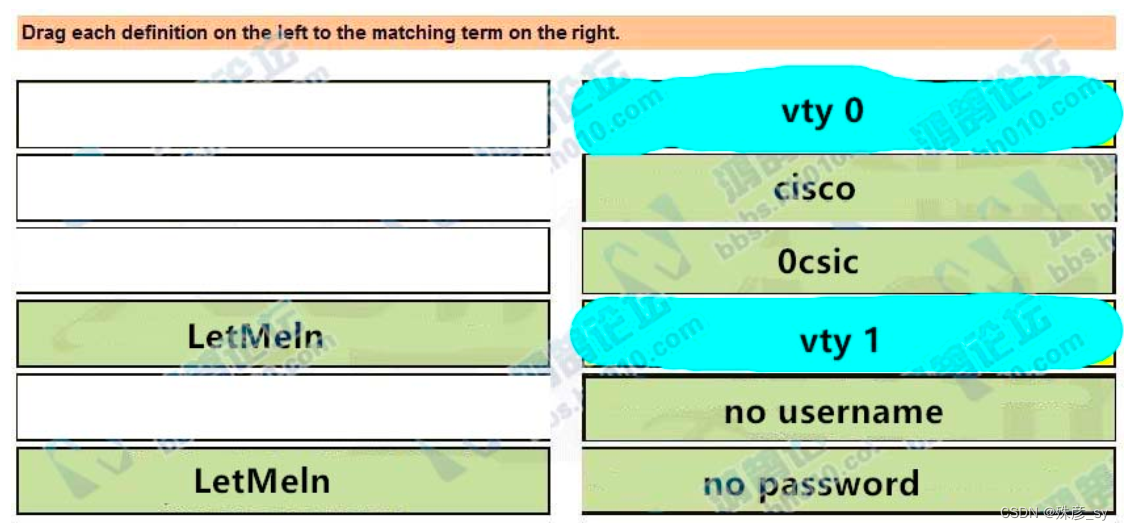
81、 Drag and drop the credentials from the left onto the remote login information on the right to resolve a failed login attempt to vtys. Not all credentials are
used.
aaa new-model
aaa authentication login default none
aaa authentication login telnet local
!
username cisco password 0 Ocsic
!
line vty 0
password LetMeIn
login authentication telnet
transport input telnet
line vty 1
password LetMeIn
transport input telnet
82、Refer to the exhibit. An engineer is monitoring reachability of the configured default routes to ISP1 and ISP2. The default route from ISP1 is preferred if available.
How is this issue resolved?
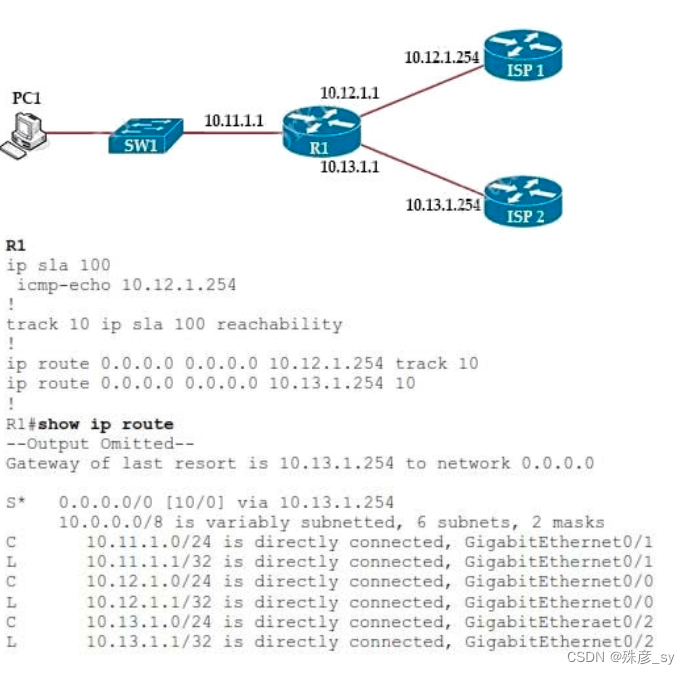
A. Use the icmp-echo command to track both default routes
B. Start IP SLA by matching numbers for track and ip sla commands
C. Start IP SLA by defining frequency and scheduling it
D. Use the same AD for both default routes
83、Refer to the exhibit. Redistribution is enabled between the routing protocols, and now PC2 PC3, and PC4 cannot reach PC1. What are the two solutions to fix the problem? (Choose two)
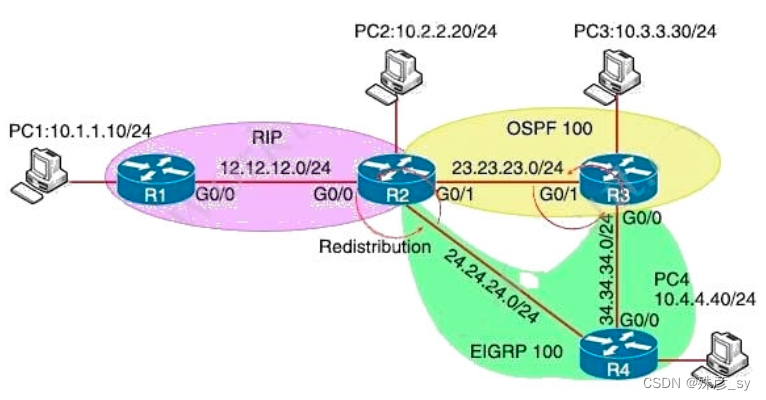
A. Filter RIP and OSPF routes back into OSPF from EIGRP when redistributing into OSPF in R2
B. Filter all routes except EIGRP routes when redistributing into OSPF in R3
C. Filter OSPF routes into RIP from EIGRP when redistributing into RIP in R2
D. Filter all routes except RIP routes when redistributing into EIGRP in R2
E. Filter RIP routes back into RIP when redistributing into RIP in R2
84、 Which label operations are performed by a label edge router?
A. PUSH and PHP
B. SWAP and POP
C. SWAP and PUSH
D. PUSH and POP
85、Refer to the exhibit. The network administrator configured VRF lite for customer A. The technician at the remote site misconfigured VRF on the router.
Which configuration will resolve connectivity for both sites of customer A?
ip vrf customer_a
rd 1:1
route-target export 1:1
route-target import 1:1
!
interface FastEthernetO.1
encapsulation dot1Q 2
ip vrf forwarding customer_a
ip address 192.168.4.1 255.255.255.0
!
router ospf 1
log-adj adjacency-changes
!
router ospf 2 vrf customer_a
log-adj adjacency-changes
network 192.168.4.0 0.0.0.255 area 0
!
end
A. ip vrf customer_a
rd 1:2
route-target both 1:1
B. ip vrf customer_a
rd 1:2
route-target both 1:2
C. ip vrf customer_a
rd 1:1
router-target import 1:1
router-target export 1:2
D. ip vrf customer_a
rd 1:1
route-target export 1:2
router-target import 1:2
86、Drag and drop the operations from the left onto the locations where the operations are performed on the right.
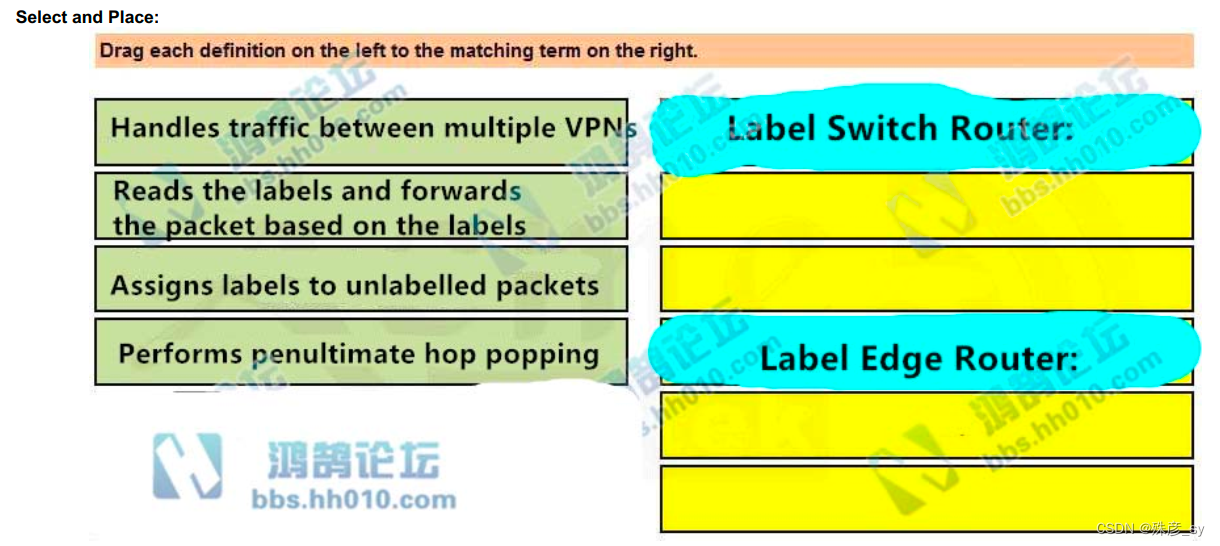
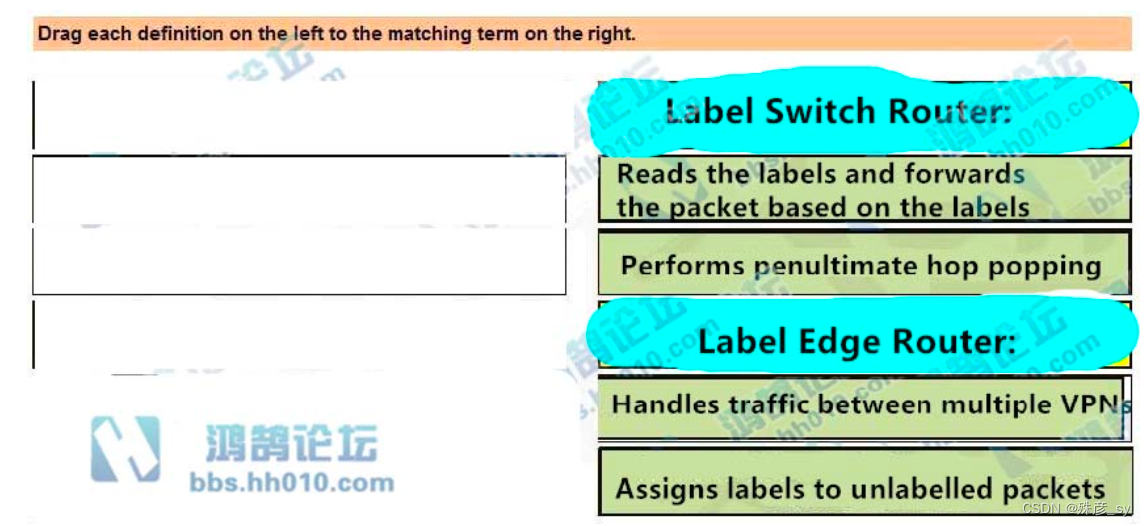
87、After some changes in the routing policy, it is noticed that the router in AS 45123 is being used as a transit AS router for several service providers.
Which configuration ensures that the branch router in AS 45123 advertises only the local networks to all SP neighbors?
A. ip as-path access-list 1 permit ^45123$
!
router bgp 45123
neighbor SP-Neighbors filter-list 1 out
B. ip as-path access-list 1 permit ^45123
!
router bgp 45123
neighbor SP-Neighbors filter-list 1 out
C. ip as-path access-list 1 permit ^$!
router bgp 45123
neighbor SP-Neighbors filter-list 1 out
D. ip as-path access-list 1 permit
!
router bgp 45123
neighbor SP-Neighbors filter-list 1 out
88、 Refer to the exhibit. An engineer is trying to get a packet destined for 192.168.32.100 forwarded through 10.1.1.1, but it was forwarded through 10.1.1.2.
What action forwards the packets through 10.1.1.1?
Router#show ip route
...
D 192.168.32.0/19 [90/25789217] via 10.1.1.1
R 192.168.32.0/24 [120/4] via 10.1.1.2
O 192.168.32.0/26 [110/229840] via 10.1.1.3
A. Configure EIGRP to receive 192.168.32.0 route with lower metric
B. Configure EIGRP to receive 192.168.32.0 route with lower administrative distance
C. Configure EIGRP to receive 192.168.32.0 route with equal or longer prefix than /24
D. Configure EIGRP to receive 192.168.32.0 route with longer prefix than /19
89、Refer to the exhibit. A junior engineer updated a branch router configuration. Immediately after the change, the engineer receives calls from the help desk that branch personnel cannot reach any network destinations. Which configuration restores service and continues to block 10.1.1.100/32?
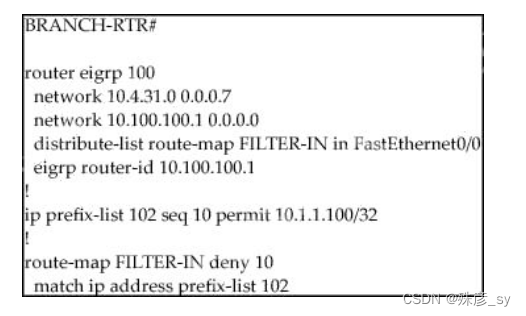
A. ip prefix-list 102 seq 15 permit 0.0.0.0/32 le 32
B. route-map FILTER-IN permit 20
C. ip prefix-list 102 seq 5 permit 0.0.0.0/32 le 32
D. route-map FILTER-IN deny 5
90、 An engineer configured a leak-map command to summarize EIGRP routes and advertise specifically loopback 0 with an IP of 10.1.1.1 255.255.255.252
along with the summary route. After finishing configuration, the customer complained not receiving summary route with specific loopback address.
Which two configurations will fix it? (Choose two)
router eigrp 1
!
route_map Leak-Route deny 10
!
interface Serial 0/0
ip summary-address eigrp 1 10.0.0.0 255.0.0.0 leak-map Leak-Route
A. Configure route-map Leak-Route permit 10 and match access-list 1
B. Configure access-list 1 permit 10.1.1.1 0.0.0.252
C. Configure access-list 1 and match under route-map Leak-Route
D. Configure route-map Leak-Route permit 20
E. Configure access-list 1 permit 10.1.1.0 0.0.0.3
91、Refer to the exhibit. An IP SLA is configured to use the backup default route when the primary is down, but it is not working as desired. Which command
fixes the issue?
R1(config)#ip route 0.0.0.0 0.0.0.0 1.1.1.1
R1(config)#ip route 0.0.0.0 0.0.0.0 2.2.2.2 10
R1(config)#ip sla 1
R1(config)#icmp-echo 1.1.1.1 source-interface FastEthernet0/0
R1(config)#ip sla schedule 1 life forever start-time now
R1(config)#track 1 ip sla 1 reachability
A. R1(config)# ip route 0.0.0.0 0.0.0.0 1.1.1.1 track 1
B. R1 (config)# ip route 0.0.0 0 0.0.0 0 2.2.2 2
C. R1 (config)# ip route 0.0.0.0 0.0.0.0 2.2.2.2 10 track 1
D. R1(config)# ip sla track 1
92、What is an advantage of using BFD
A. It detects local link failure at layer 1 and updates routing table
B. It detects local link failure at layer 3 and updates routing protocols
C. It has sub-second failure detection for layer 1 and layer 2 problems
D. It has sub-second failure detection for layer 1 and layer 3 problems
93、Refer to the exhibit. The ACL is placed on the inbound GigabitEthernet 0/1 interface of the router. Host 192.168.10.10 cannot SSH to host 192.168.100.1 even though the flow is permitted. Which action resolves the issue without opening full access to this router?
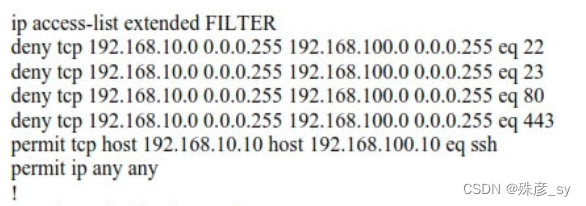
ip address 192.168.10.1 255.255.255.0
ip access-group FILTER in
A. Temporarily move the permit ip any any line to the beginning of the ACL to see if it the flow works
B. Run the show access-list FILTER command to view if the SSH entry has any hit statistics associated with it
C. Move the SSH entry to the beginning of the ACL
D. Temporarily remove the ACL from the interface to see if the flow works
94、Which component of MPLS VPN is used to extend the IP address so that an engineer is able to identify to which VPN it belongs?
A. RD
B. VPNv4 address family
C. RT
D. LDP
95、Refer to the exhibit. BGP is flapping after the CoPP policy is applied. What are the two solutions to fix the issue? (Choose two)
policy-mapp COPP-7600
class COPP-CRITICAL-7600
police cir 2000000 bc 62500
conform-action transmit
exceed-action transmit
!class class-default
police cir 2000000 bc 6250
conform-action transmit
exceed-action drop
!
class-map match-all COPP-CRITICAL-7600
match access-group name COPP-CRITICAL-7600
!
ip access-list extended COPP-CRITICAL-7600
permit ip any any eq http
permit ip any any eq https
A. Configure BGP in the COPP-CRITICAL-7600 ACL
B. Configure a higher value for CIR under the default class to allow more packets during peak traffic
C. Configure a higher value for CIR under the class COPP-CRITICAL-7600
D. Configure a three-color policer instead of two-color policer under class COPP-CRITICAL
E. Configure IP CEF to CoPP policy and BGP to work
96、Drag and drop the MPLS VPN device types from the left onto the definitions on the right.
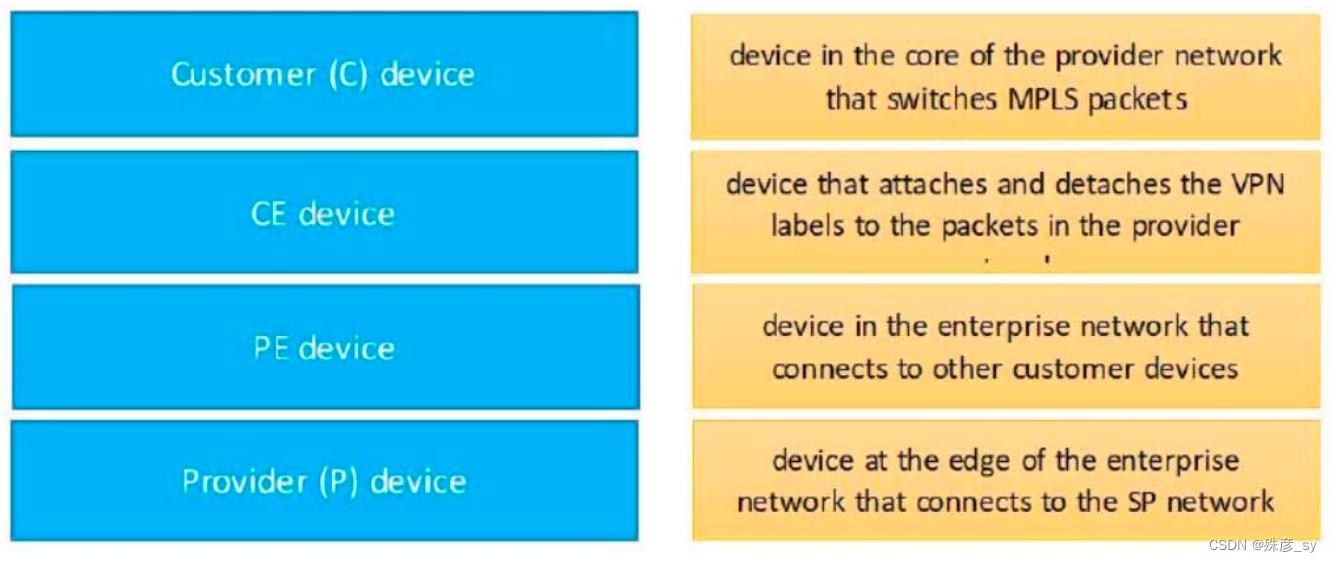

97、
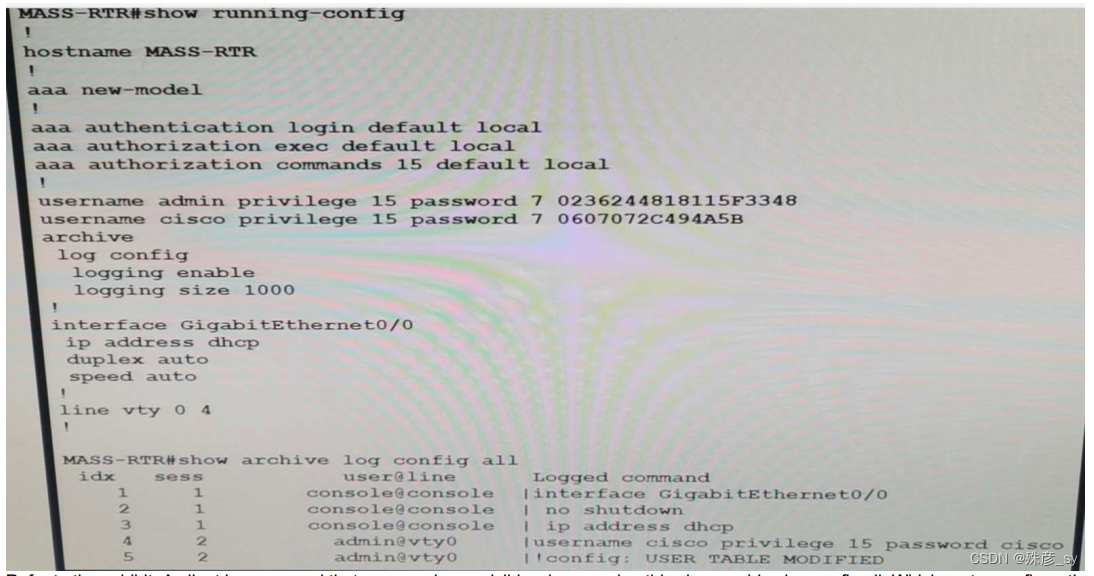 Refer to the exhibit. A client is concerned that passwords are visible when running this show archive log config all. Which router configuration is needed to resolve
Refer to the exhibit. A client is concerned that passwords are visible when running this show archive log config all. Which router configuration is needed to resolve
this issue?
A. MASS-RTR(config-archive-log-cfg)#hidekeys
B. MASS-RTR(config)#service password-encryption
C. MASS-RTR(config)#aaa authentication arap
D. MASS-RTR(config-archive-log-cfg)#password encryption aes
98、
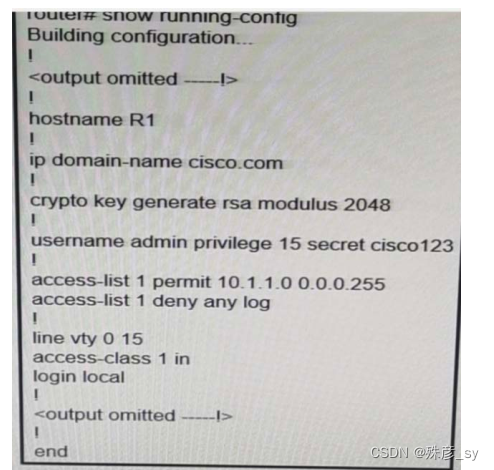
Refer to the exhibit. A user cannot SSH to the router. What action must be taken to resolve this issue?
A. Configure transport input ssh
B. Configure transport output ssh
C. Configure ip ssh version 2
D. Configure ip ssh source-interface loopback0
99、
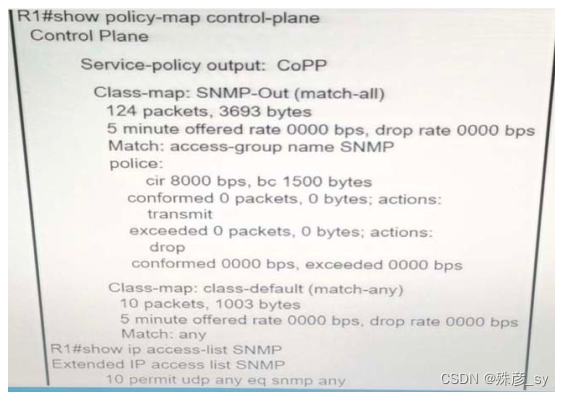
Refer to the exhibit. R1 is being monitored using SNMP and monitoring devices are getting only partial information. What action should be taken to resolve this
issue?
A. Modify the CoPP policy to increase the configured exceeded limit for SNMP
B. Modify the access list to include snmptrap.
C. Modify the CoPP policy to increase the configured CIR limit for SNMP
D. Modify the access list to add a second line to allow udp any any eg snmp
100、
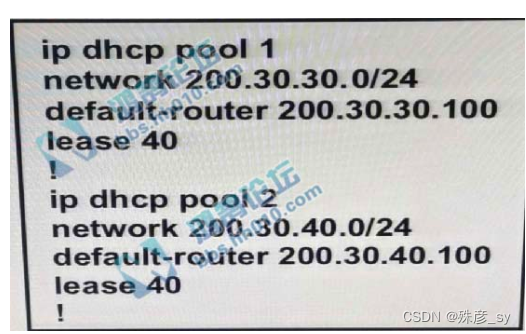
Refer to the exhibit. The server for the finance department is not reachable consistently on the 200.30.40.0/24 network and after every second month it gets a new
IP address. What two actions must be taken to resolve this issue? (Choosetwo.)
A. Configure the server to use DHCP on the network with default gateway 200.30.40.100.
B. Configure the server with a static IP address and default gateway
C. Configure the router to exclude a server IP address
D. Configure the server to use DHCP on the network with default gateway 200.30.30.100.
E. Configure the router to exclude a server IP address and default gateway
